TLS/SSL authentication and encryption methods can be applied to the socket layer to secure Internet or network communication.
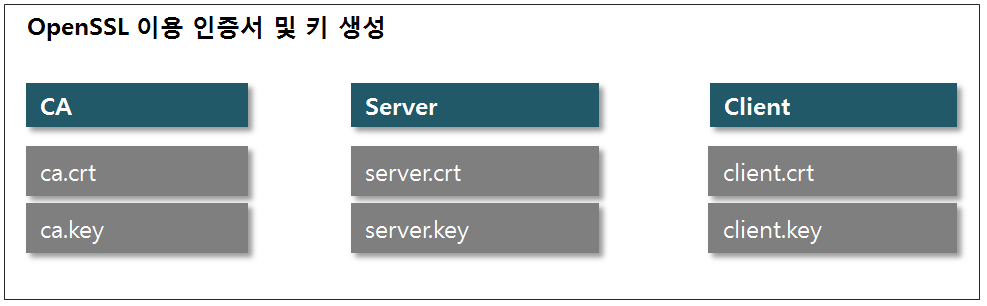
For TLS/SSL encryption, various certificates and encryption keys are basically required as shown in the figure below.
This page shows an example of generating encryption keys and certificates required for TCP/UDP, HTTPS, and MQTTS using OpenSSL.
♦ Refer to OpenSSL 설치하기 | momoiot for OpenSSL installation.
1. Generating the CA key and certificate
| Procedure | Command |
| Path to OpenSSL/bin | |
| CA security key generation | OpenSSL/bin>openssl genrsa -des3 -out ca.key 2048 |
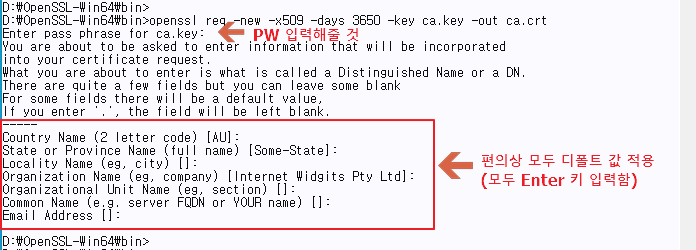
| CA certificate generation | OpenSSL/bin>openssl req -new -x509 -days 3650 -key ca.key -out ca.crt |
♦ CA security key generation
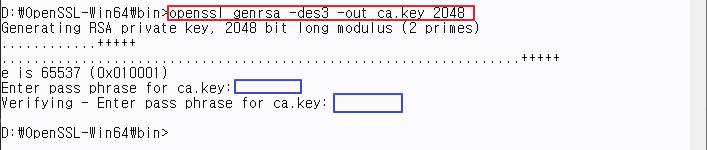 |
ca.key value= input arbitrarily. |
| Recheck the ca.key value. |
♦ CA certificate generation
 |
|
2. Generating the server key and certificate
| Procedure | Command |
| Server security key generation | openssl/bin>openssl genrsa -out server.key 2048 |
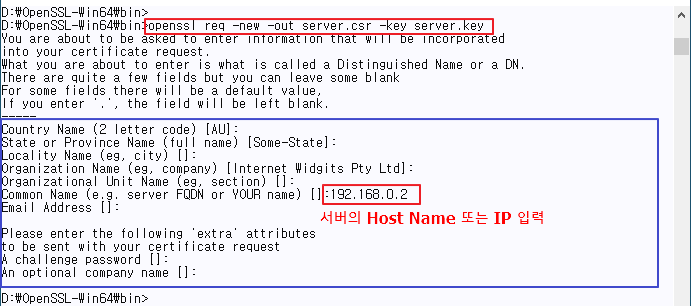
| Generate a CSR | openssl/bin>openssl req -new -out server.csr -key server.key |
|
Send CSR to CA & Generate server certificate |
openssl/bin>openssl x509 -req -in server.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out server.crt -days 3650 |
| Validate the server certificate | openssl/bin>openssl verify -CAfile ca.crt server.crt |
♦ Generate server security key

⊕ OpenSSL에서 만들어진 이 보안키 파일에는 개인키와 공개키가 모두 포함되어 있다.
♦ Generate Server CSR
 |
|
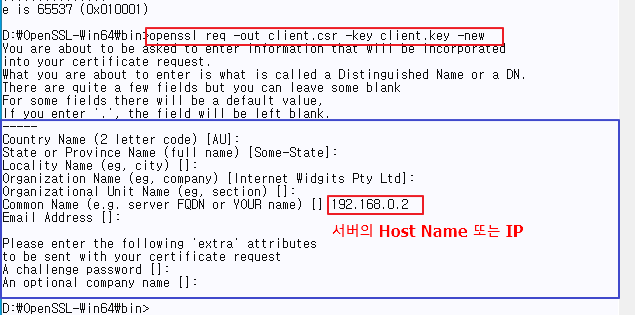
⊗ For the Common Name, there is no problem in generating a certificate even if an arbitrary value is entered.
However, for compatibility when testing in various tools, be sure to enter the Host Name or IP of the PC where the server is installed.
⊗ as possible, if Common Name is entered as Host Name, input Host Name, and vice versa if IP is entered.
(There seems to be a compatibility difference depending on the tool/PC)
♦ Send CSR to CA → CA Signing → Issue Server certificate
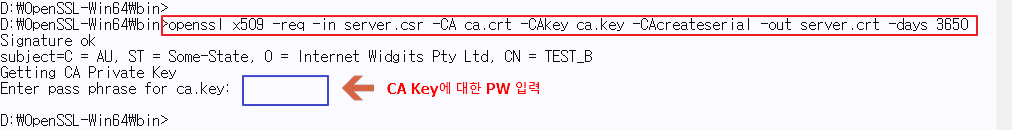
♦ Verification of the server certificate
Verify that the server certificate has been created correctly. If there is an error, it goes back and forth ~~~!
3. Generating the client key and certificate
| Procedure | Command |
| Generate client key |
openssl/bin>openssl genrsa -out client.key 2048 or for use of a pass phrase: openssl genrsa -des3 -out client.key 2048 |
| Generate Client CSR | openssl/bin>openssl req -out client.csr -key client.key -new |
| Send CSR to CA → Generate Client Certificate | openssl/bin>openssl x509 -req -in client.csr -CA ca.crt -CAkey ca.key -CAcreateserial -out client.crt -days 3650 |
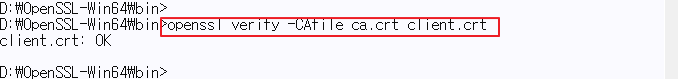
| Validating Client Certificates | openssl/bin>openssl verify -CAfile ca.crt client.crt |
⊕ openssl genrsa -out client.key, when the 2048 option is used, the pass phrase for the client key is not used.
⊕ When using MQTT.fx in a later test, it seems that the client key with pass phrase is not compatible.
The command to modify From a key with a passphrase to a key without a passphrase key is as follows.
→ openssl rsa -in client.key -out client-new.key
♦ Generate client security key
⊕ In all subsequent tests, the passphrase for the client key will not be used except in special cases.

⊕ This security key file created by OpenSSL contains both private and public keys.
♦ Generate client CSR
 |
|
♦ Send CSR to CA → CA Signing → Issue Client Certificate
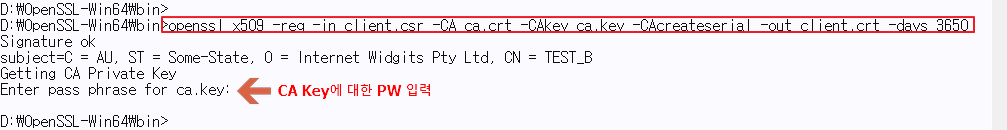
♦ Validating Client Certificates
4. Viewing certificate
> openssl x509 -in client.crt -text -noout

